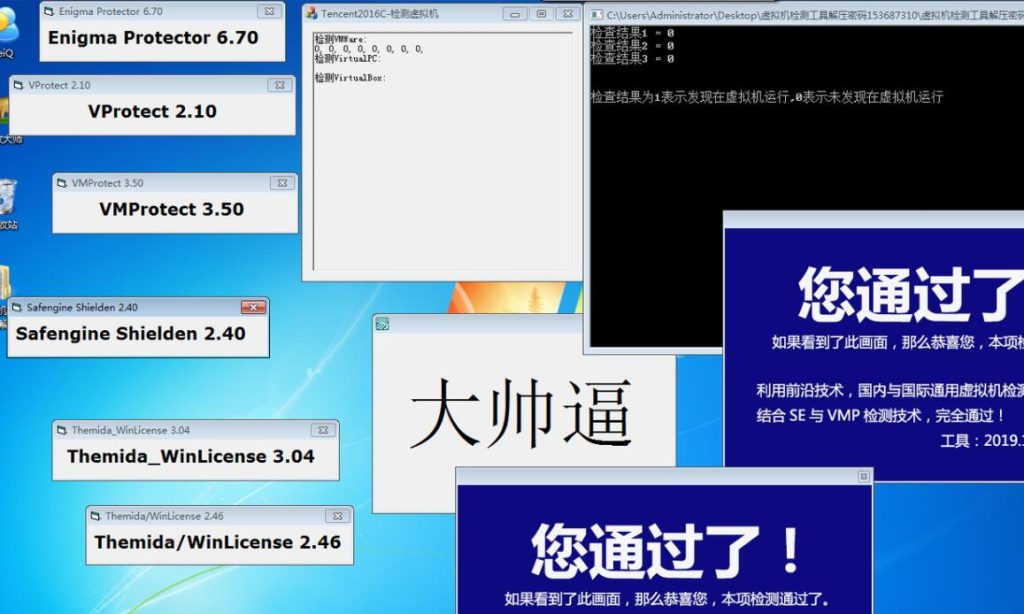
总的来说就是先改vmx撸掉cpuid的hypervisor present bit和几个后门特权指令
然后特征定位到管理SystemFirmwareTable的链表,把里面填充信息的handler接管了,请求firmware信息时,先在缓存里面搜索特征”VMWare” “Virtual”有就屏蔽掉。
支持win7和win10
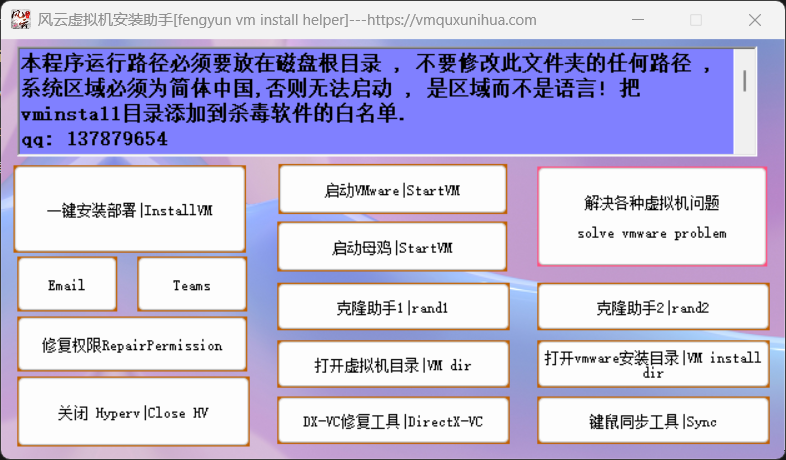
源码下载,需要安装WDK, 编译后放在vm虚拟机里面,运行bat即可
使用方法:
1:vmx配置
hypervisor.cpuid.v0 = "FALSE"
board-id.reflectHost = "TRUE"
hw.model.reflectHost = "TRUE"
serialNumber.reflectHost = "TRUE"
smbios.reflectHost = "TRUE"
SMBIOS.noOEMStrings = "TRUE"
isolation.tools.getPtrLocation.disable = "TRUE"
isolation.tools.setPtrLocation.disable = "TRUE"
isolation.tools.setVersion.disable = "TRUE"
isolation.tools.getVersion.disable = "TRUE"
monitor_control.disable_directexec = "TRUE"
monitor_control.disable_chksimd = "TRUE"
monitor_control.disable_ntreloc = "TRUE"
monitor_control.disable_selfmod = "TRUE"
monitor_control.disable_reloc = "TRUE"
monitor_control.disable_btinout = "TRUE"
monitor_control.disable_btmemspace = "TRUE"
monitor_control.disable_btpriv = "TRUE"
monitor_control.disable_btseg = "TRUE"
monitor_control.restrict_backdoor = "TRUE"2:如果有scsi硬盘,则vmx添加
scsi0:0.productID = "硬盘名称 SSD"
scsi0:0.vendorID = "硬盘名称"3:修改mac地址,前面2个默认56:4D,改为其他即可,如图中00:10
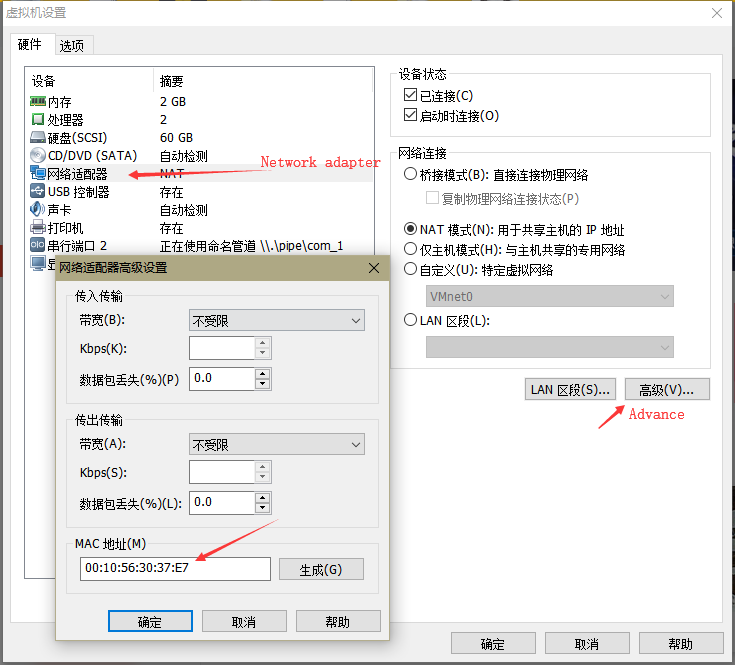
4: 在vm里面运行bat文件即可
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END





- 最新
- 最热
只看作者